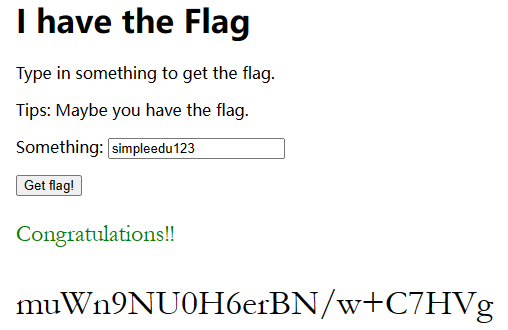
MISC i have the flag 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 function ck (s ) { try { ic } catch (e) { return ; } var a = [118 , 108 , 112 , 115 , 111 , 104 , 104 , 103 , 120 , 52 , 53 , 54 ]; if (s.length == a.length ) { for (i = 0 ; i < s.length ; i++) { if (a[i] - s.charCodeAt (i) != 3 ) return ic = false ; } return ic = true ; } return ic = false ; } # 题目js代码,只要条件为真即可
1 2 3 4 5 6 def add (num ): return num-3 a = [118 , 108 , 112 , 115 , 111 , 104 , 104 , 103 , 120 , 52 , 53 , 54 ] print ('' .join(list (map (chr ,list (map (add,a))))))
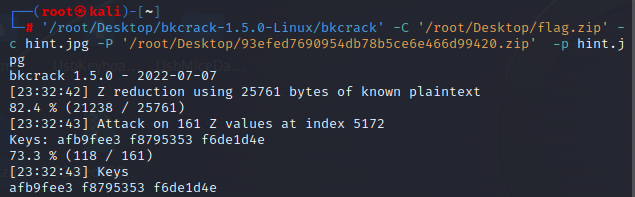
幸运饼干 1 2 3 4 # Bkcrack 明文爆破 '/root/Desktop/bkcrack-1.5.0-Linux/bkcrack' -C '/root/Desktop/flag.zip' -c hint.jpg -P '/root/Desktop/93efed7690954db78b5ce6e466d99420.zip' -p hint.jpg # afb9fee3 f8795353 f6de1d4e
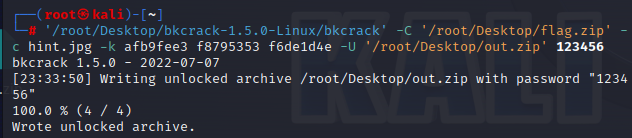
1 2 # 修改密码 '/root/Desktop/bkcrack-1.5.0-Linux/bkcrack' -C '/root/Desktop/flag.zip' -c hint.jpg -k afb9fee3 f8795353 f6de1d4e -U '/root/Desktop/out.zip' 123456
1 2 3 4 5 6 7 8 9 10 # 获取password * NTLM : 786515ed10d6b79e74c1739f72a158cc > 54231 # 获取masterkey mimikatz # dpapi::masterkey /in:C:\Users\HK\Desktop\out\S-1-5-21-726299542-2485387390-1117163988-1001\e5f8e386-7041-4f16-b02d-304c71040126 /password:54231 > key : 7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac # 解密cookie mimikatz # dpapi::chrome /in:C:\Users\HK\Desktop\out\Cookies /masterkey:7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac > Cookie: flag{mimikatz_is_bravo_xz12ss}
jpginside 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 ''' store = [ 111, 217, 97, ... ... 116, 101, 49, 50] key = raw_input('Please input the key:') with open('excellent.jpg', 'wb') as jpg: for i in range(len(store)): jpg.write(chr(store[i] ^ ord(key[i % len(key)]))) ''' ''' store = [ 111, 217, 97, ... ... 116, 101, 49, 50] key = b'rotate1234!' with open('excellent.jpg', 'wb') as jpg: for i in range(len(store)): jpg.write(bytes([store[i] ^ key[i % len(key)]])) ''' import binasciidata = [141 , 183 , 139 , 129 , 116 , 117 , 123 , 116 , 122 , 114 , 33 , 115 , 110 , 117 , 97 , ] jpg = binascii.unhexlify('FFD8FFE000104A4649460001010101' ) data = bytes (data) print (len (jpg),len (data))out = '' for i in range (len (data)): out += chr (data[i] ^ jpg[i]) print (out)
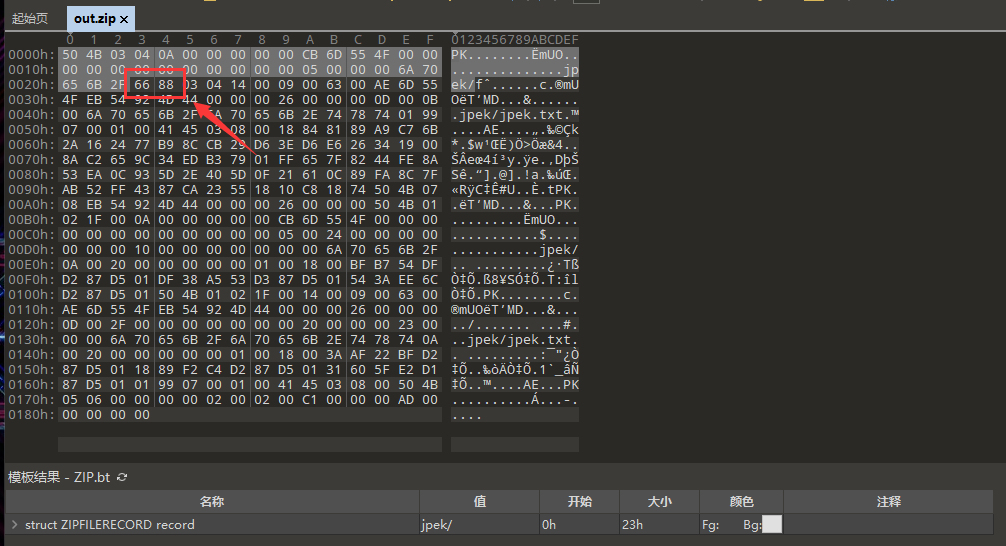
执行之前修复好的代码,本地生成了excellent.jpg,分离末尾的zip文件
1 2 jpek{39i0jf49229fie5j33f02403hj953012} rot22: flag{39e0fb49229bea5f33b02403df953012}
数独 1 gaps run '/root/Desktop/image.png' '/root/Desktop/out.png' --size=70