2023 极客大挑战 MISC WP
MISC
ez_smilemo
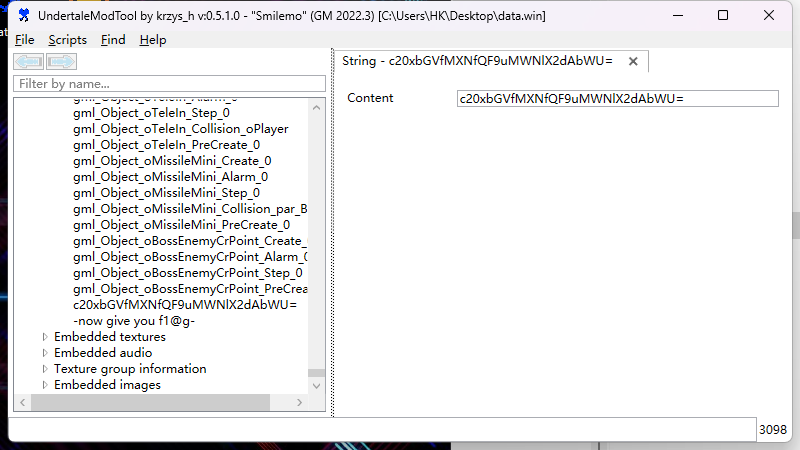
1 | UndertaleModTool解包data.win,在字符串最后的内容中找到flag |
Qingwan的心要碎了
1 | 百度识图: |
时代的眼泪
1 | 取证大师 -> 最近访问 -> 图片内容 |
下一站是哪儿呢
1 | airport.png |
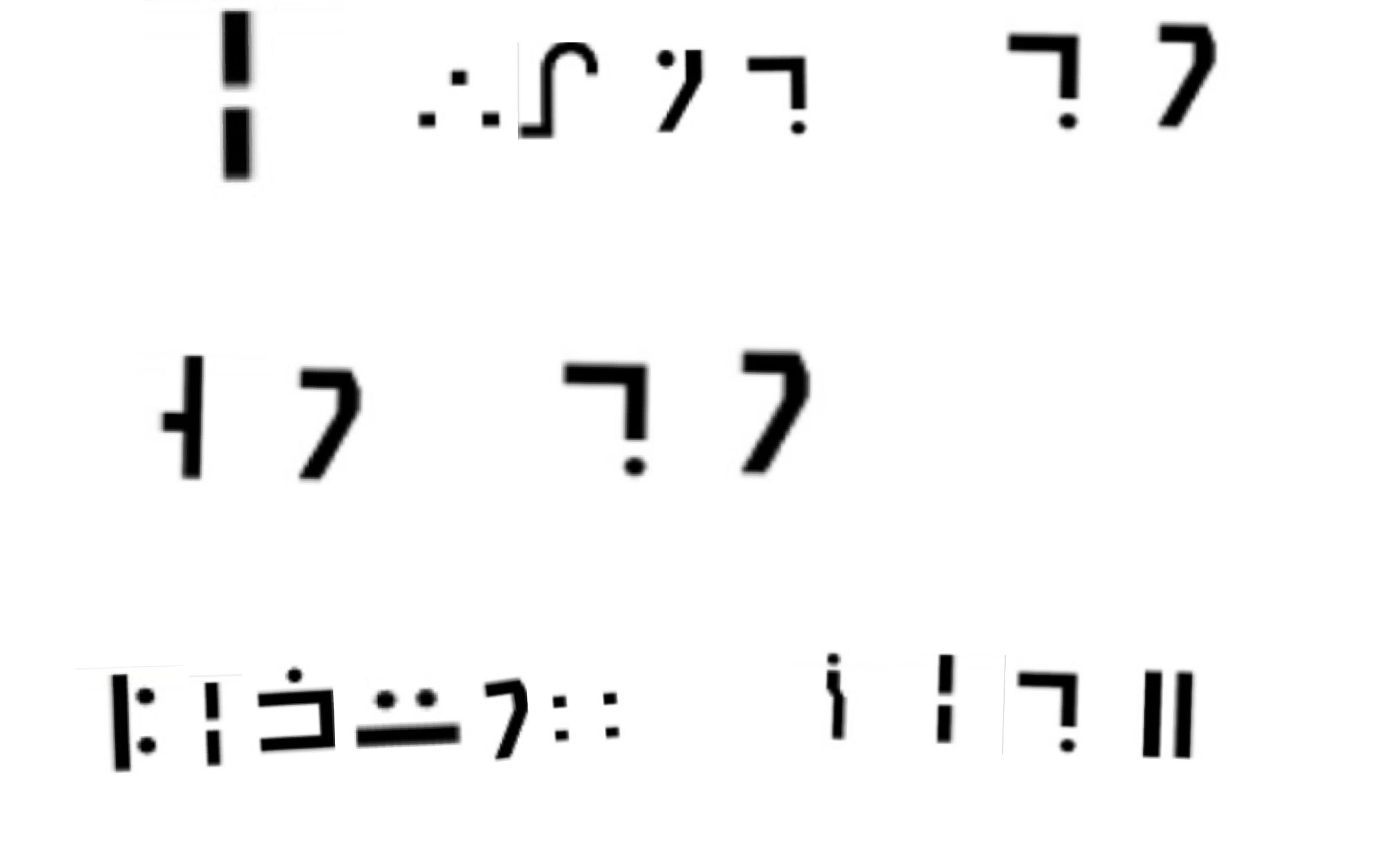
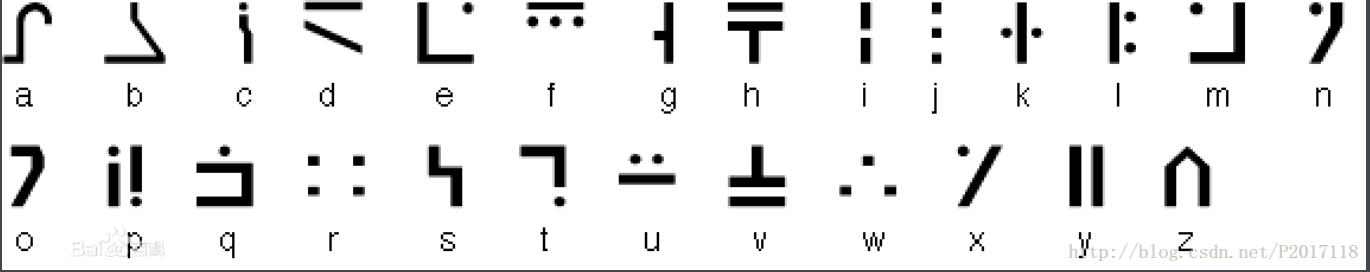
1 | 对照码表得到 |
xqr
1 | # 分离出需要异或的图片 |
1 | from PIL import Image |
异或
反色
1 | SYC{hOp3_u_h@ve_Fun} |
extractMe
1 | import binascii |
DEATH_N0TE
1 | from PIL import Image |


1 | 省略此步骤,复现对照码表麻烦 |
1 | >>> zsteg kamisama.png |
DEATH_N1TE
1 | from PIL import Image |
多图拼接
1 | gaps run 'input.png' 'output.png' --size=48 |

L.mp3中间部分使用mmsstv,得到图像
1 | SYC{H4xr0t0r__14_Ki114R} |
DEATH_N2TE
1 | import cv2 |
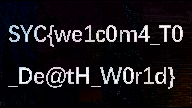
1 | SYC{we1c0m4_T0_De@th_W0r1d} |
窃听风云
NTLM解密
1 | No.7流内容 |
窃听风云V2
1 | 思路如上,不过V2在wireshark里base64内容不会被wireshark解析,需要手动根据特征对照出具体内容 |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 IHK-1's blog!