MISC
oversharing
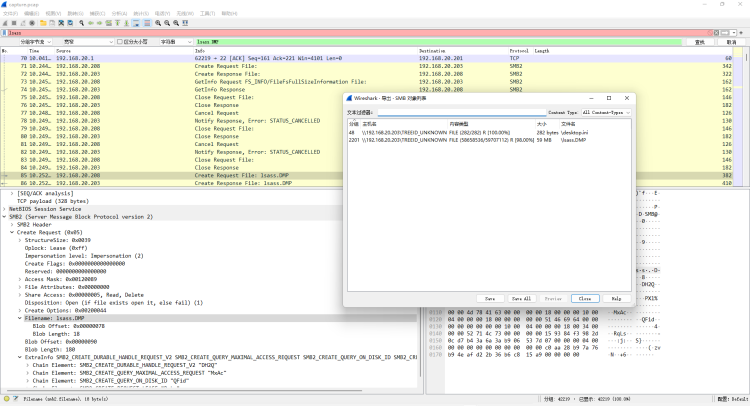
文件中有lsass.DMP ,使用 mimikatz 进行提取用户密码
导出 lsass.DMP 修改文件名为 lsass.dmp 并使用 mimikatz x64 载入
1
2
| sekurlsa::minidump lsass.dmp
sekurlsa::logonpasswords full
|
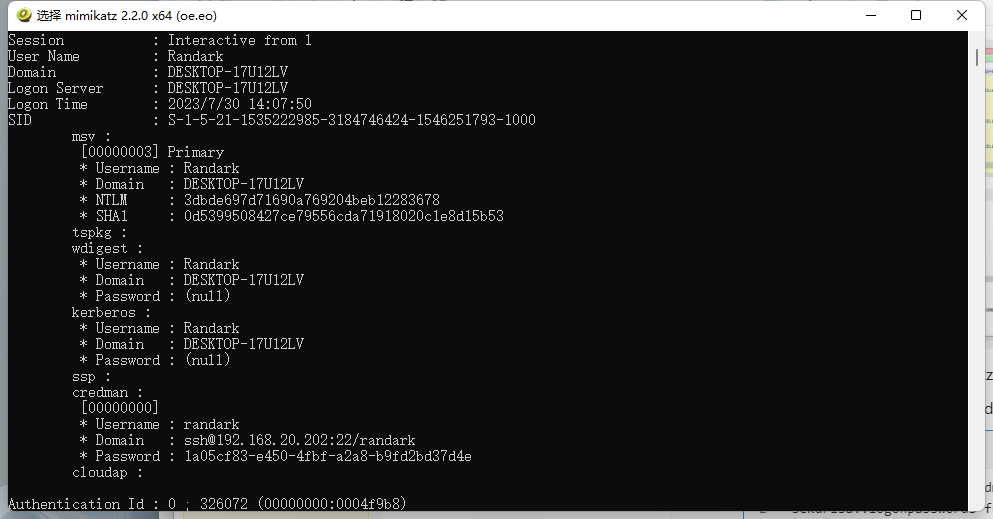
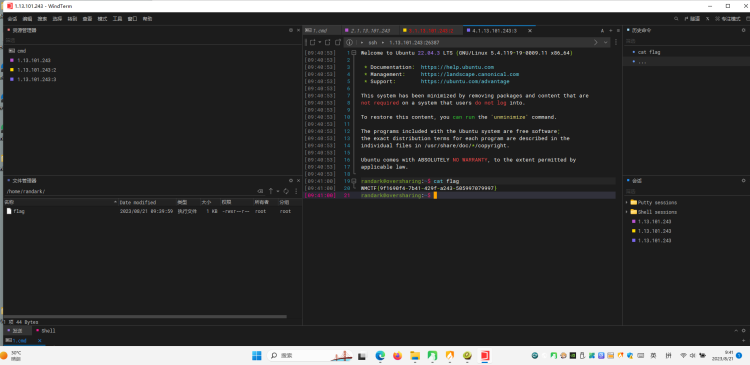
获得 ssh 的用户名与密码
1
2
3
4
5
| * Domain : ssh@192.168.20.202:22/randark
* Password : 1a05cf83-e450-4fbf-a2a8-b9fd2bd37d4e
cat flag
WMCTF{9f1690f4-7b41-429f-a243-505997079997}
|
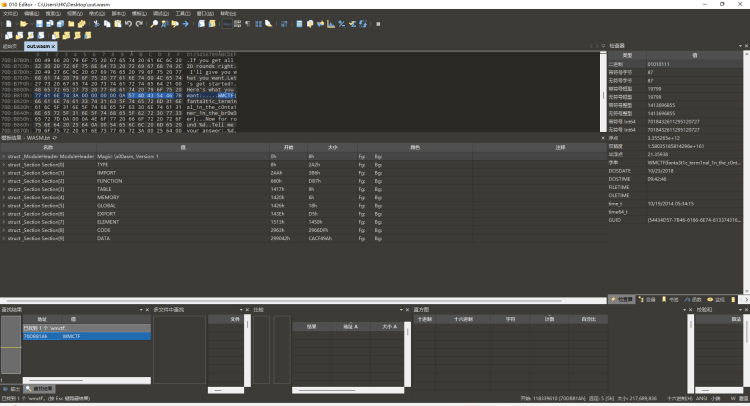
Fantastic terminal
非预期解,在 out.warms 中读取flag
1
| WMCTF{fanta3t1c_term1nal_1n_the_c0nta1ner_1n_the_br0w3er}
|
Fantastic terminal Rev
此题修复了之前的可以直接从 out.warms 读取flag
1
2
| docker build -t wmctf .
docker run -it wmctf
|
启动终端后
1
2
3
4
5
6
7
8
9
| cd challenge
base64 challenge
因为要获取challenge这个文件,但是直接cat字符编码是错误的,最好是将源文件可以完整保存下来
f0VMRgIBAQAAAAAAAAAAAAMAPgABAAAAYBEAAAAAAABAAAAAAAAAAEAxAAAAAAAAAAAAAE
...
...
AAAAAAAAAAAAAAAAAA==
|
base64 解码后将 challenge 在IDA中进行反编译
动态调试获得flag

1
| WMCTF{r3venge_terminal_after_fuck1ng_paatchhhhhhhhhhhhh}
|
STEG
EZ_V1dio
下载得到 avi 音频,尝试分离每一帧
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| import cv2
import os
if not os.path.exists('frames'):
os.makedirs('frames')
video = cv2.VideoCapture('./flag.avi')
frame_count = 0
while True:
ret, frame = video.read()
if not ret:
break
filename = f'frames/frame_{frame_count}.jpg'
cv2.imwrite(filename, frame)
frame_count += 1
video.release()
|
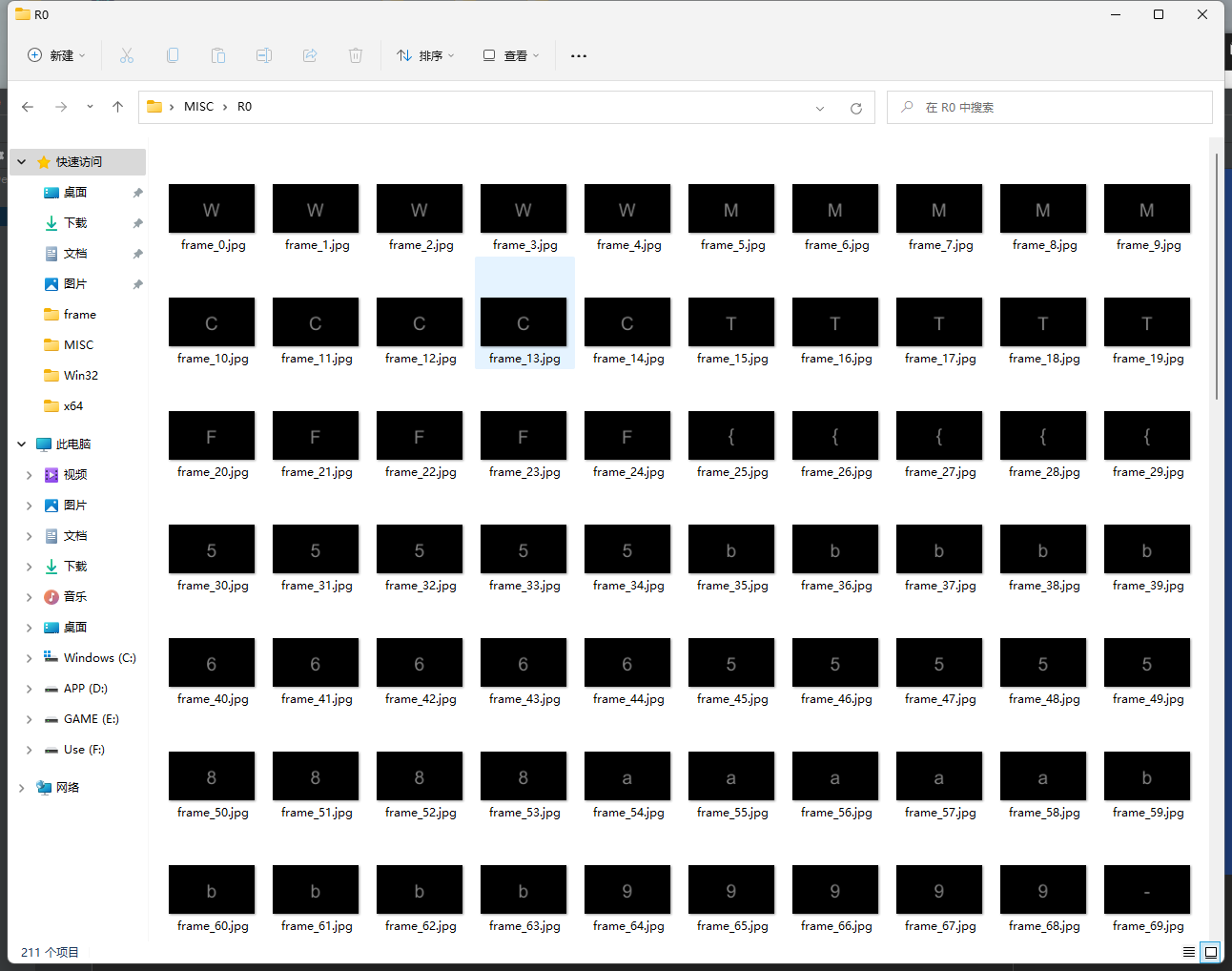
在第一帧的R0通道看到 W 字符

分离每一帧的R0通道
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| import cv2
import os
if not os.path.exists('R0'):
os.makedirs('R0')
video = cv2.VideoCapture('./flag.avi')
frame_count = 0
while True:
ret, frame = video.read()
if not ret:
break
r_channel = frame[:, :, 2] # OpenCV默认通道顺序为BGR,索引2为R通道
r_lowest_bit = r_channel & 1
r_lowest_bit <<= 7
filename = f'R0/frame_{frame_count}.jpg'
cv2.imwrite(filename, r_lowest_bit)
frame_count += 1
video.release()
|
1
2
| 去除重复后得到
WMCTF{5b658ab9-946c-3869-fc21-6ad99b3bc714}
|