2024 BeginCTF MISC WP
MISC
Tupper
1 | import base64 |
Tupper绘图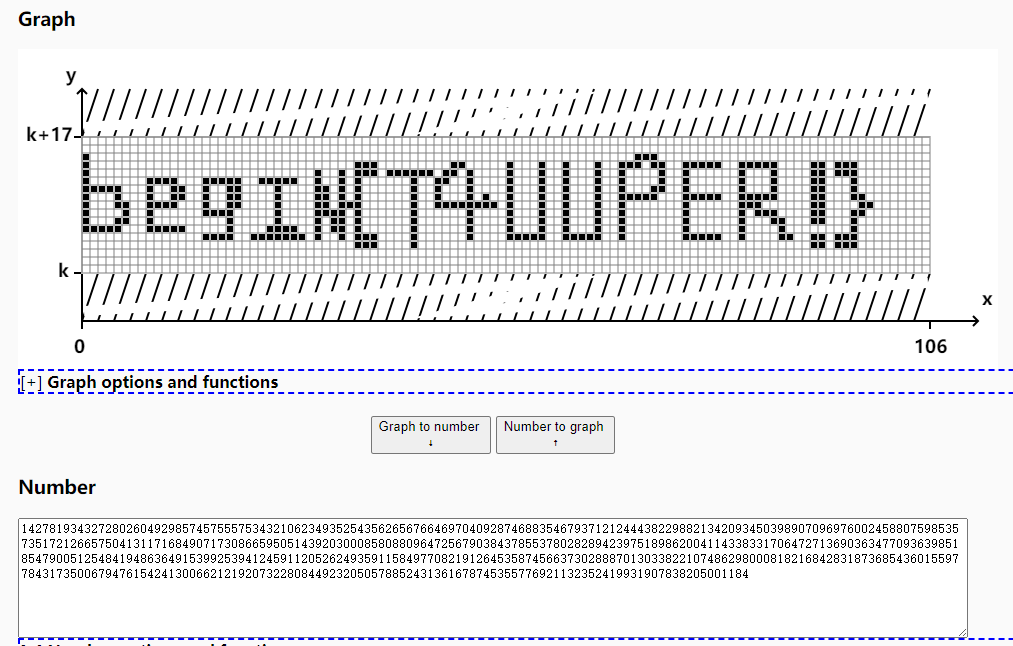
devil’s word
1 | import binascii |
下一站上岸

1 | # 一个交点 = '.' |
你知道中国文化嘛1.0
1 | # 替换字符 |
where is crazyman1.0

1 | 看着就像秋叶原 |
where is crazyman2.0

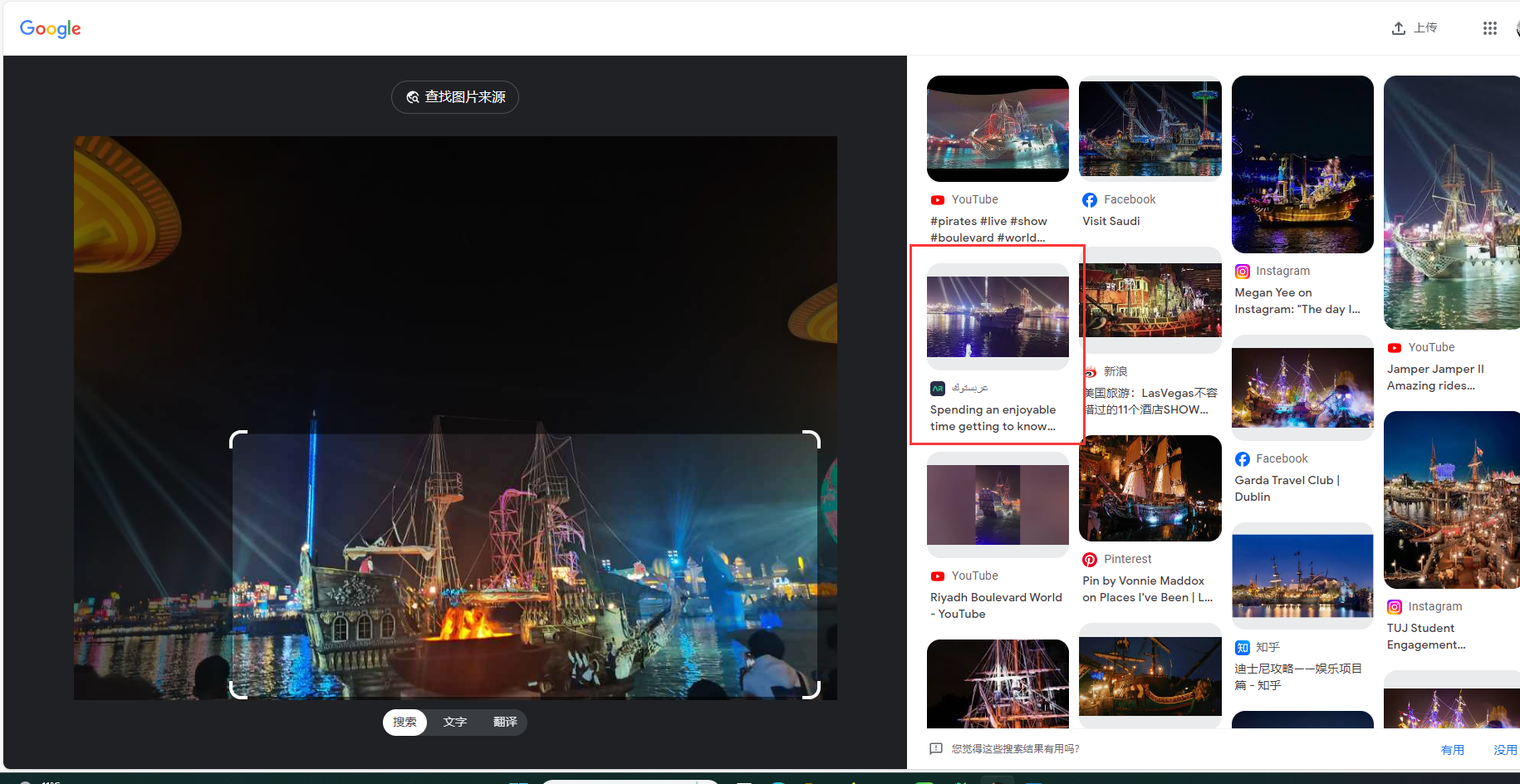
1 | # https://arabsstock.com/en/videos/clip-162878-spending-enjoyable-time-getting-know-civilizations-entertainment |
where is crazyman3.0

1 | # google关键词 "BOUDL" "STARBUCKS" "5 min walk" |
Forensics
beginner_Forensics!!!!
1 | #!/usr/bin/python |
dump dump dump
1 | # strings dumpv1.DMP | grep 'a = ' |
对照 a 的加密流程进行解密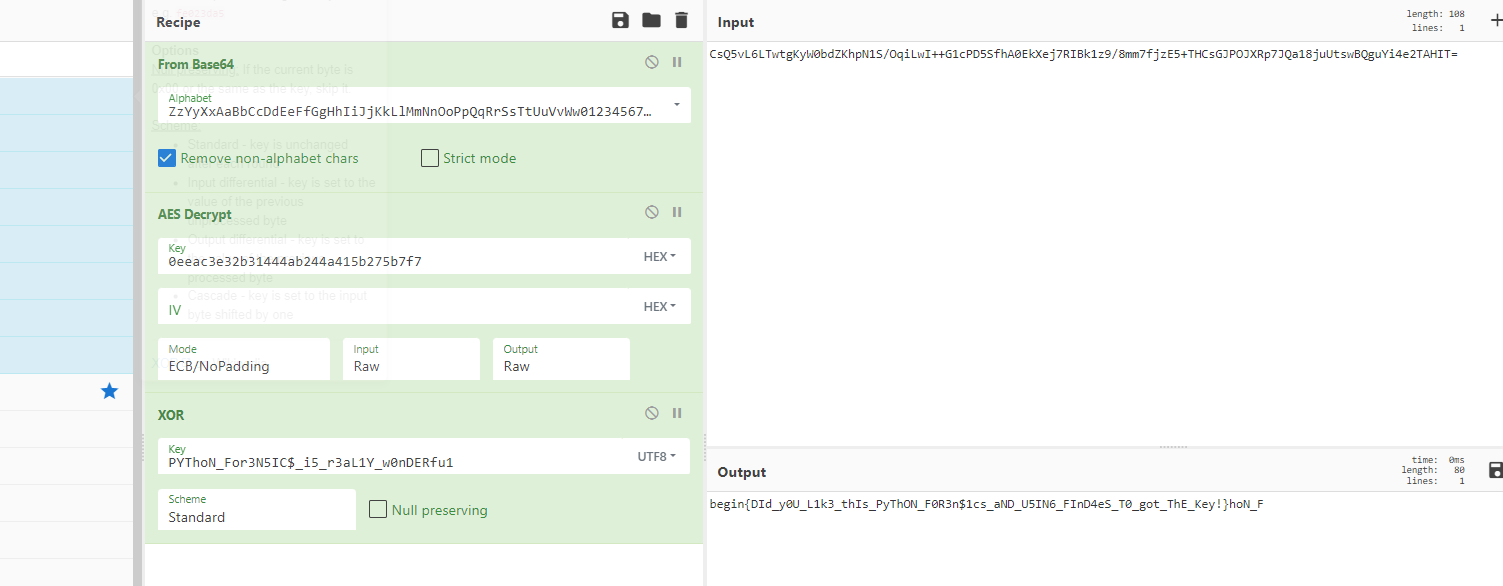
1 | begin{DId_y0U_L1k3_thIs_PyThON_F0R3n$1cs_aND_U5IN6_FInD4eS_T0_got_ThE_Key!} |
dump dump dump 2.0
1 | # strings dumpv2.DMP | grep 'a = ' |
先以 00 填充 iv ,结合 a 的加密流程进行解密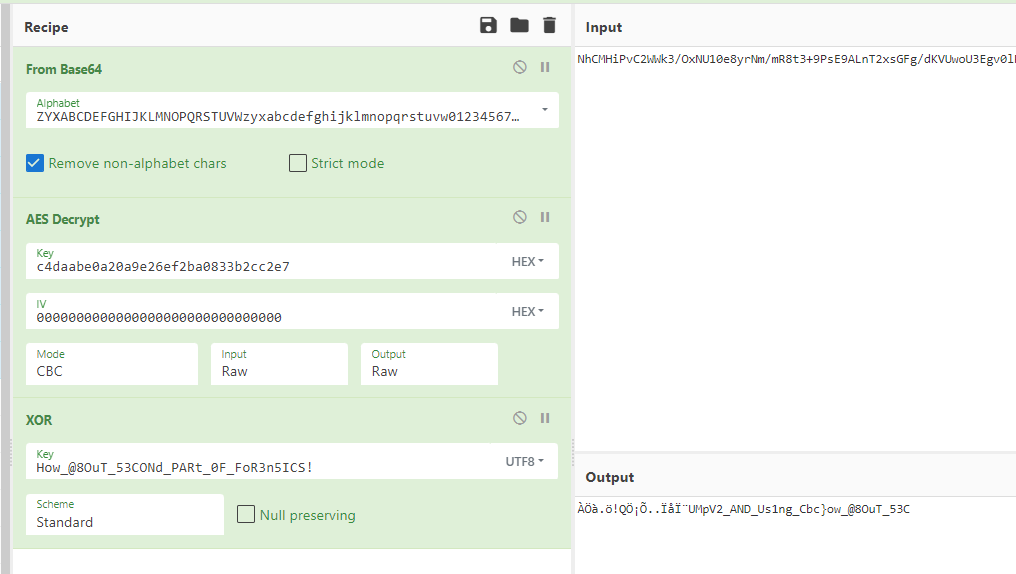
手动修改 iv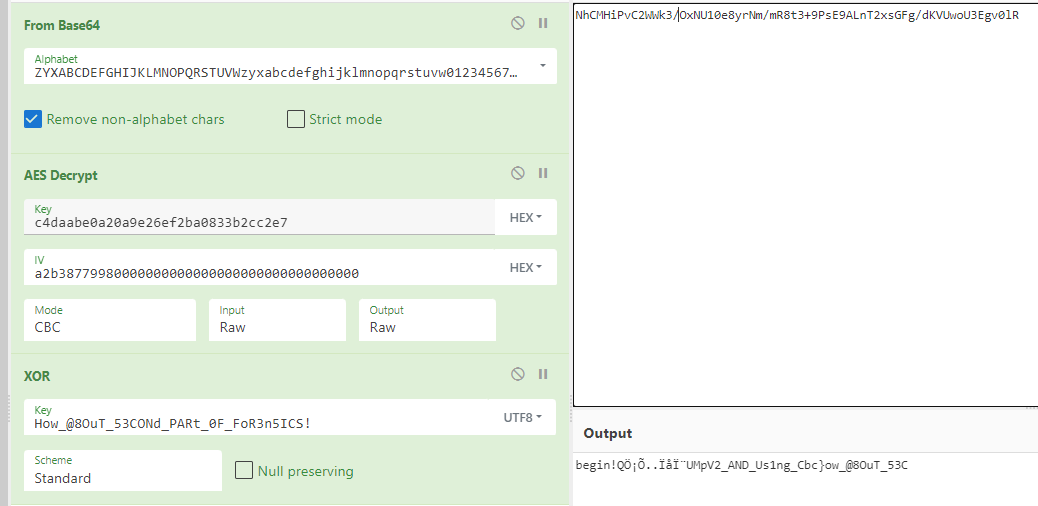
当凑齐 begin 头时 iv 为 a2b3877998 ,在010中以16进制搜索该字节
得到 iv 为 a2b38779985a25bfec905a67809790ec
补全 iv 进行解密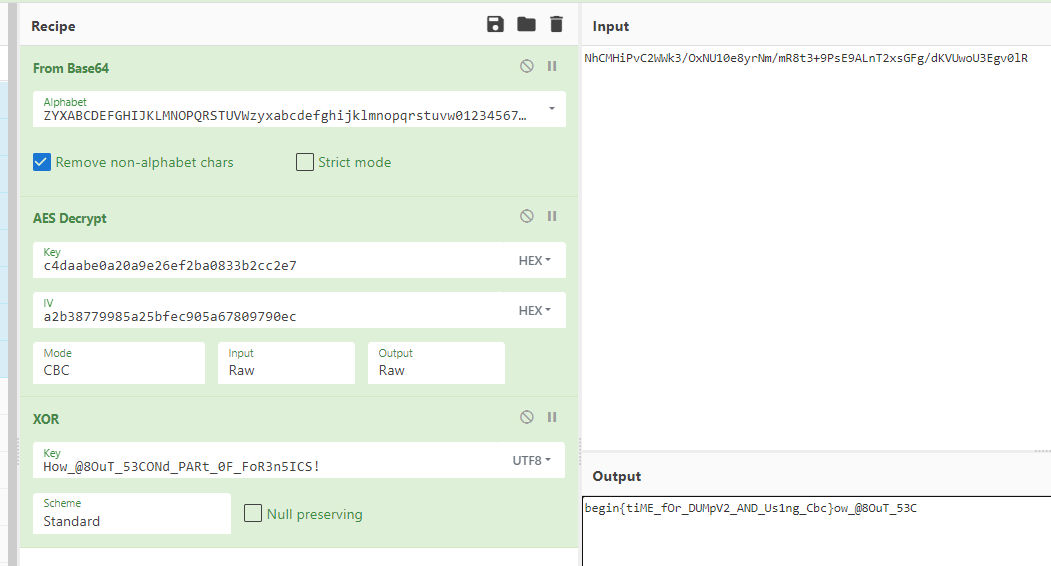
1 | begin{tiME_fOr_DUMpV2_AND_Us1ng_Cbc} |
dump dump dump 2.5
还是上题的思路,但是iv被出题人以00填充了,需要进行 CBC 字节翻转攻击
1 | # uBLJX+/zmxZn6oKVymM7t4HbVEiBvv7+kFKf/DZNHkQxF1wC0L1f4DmP5O5GO/H2HfrI+W3SdtSGJKSjVM+qO50SSxpVIJ4YTrE2r/V7bj0= |
饥渴C猫 is hacker!
1 | # https://github.com/JPaulMora/Duck-Decoder |
学取证咯 - cmd
1 | volatility.exe -f 学取证咯.raw imageinfo |
学取证咯 - 还记得ie吗?
1 | volatility.exe -f 学取证咯.raw --profile=Win7SP1x64 iehistory |
学取证咯 - 计算机的姓名?
1 | vol.py -f 学取证咯.raw --profile=Win7SP1x64 mimikatz |
学取证咯 - 想登入我的计算机吗
1 | vol.py -f 学取证咯.raw --profile=Win7SP1x64 mimikatz |
学取证咯 - 机密文件
1 | vol.py -f 学取证咯.raw --profile=Win7SP1x64 filescan | grep '机密' |
学取证咯 - 真的是取证吗?
1 | vol.py -f 学取证咯.raw --profile=Win7SP1x64 filescan | grep 'flag' |
脱入 IDA 32 ,选择字串 ‘FLAG’ ,Ctrl + X 定位,F5反编译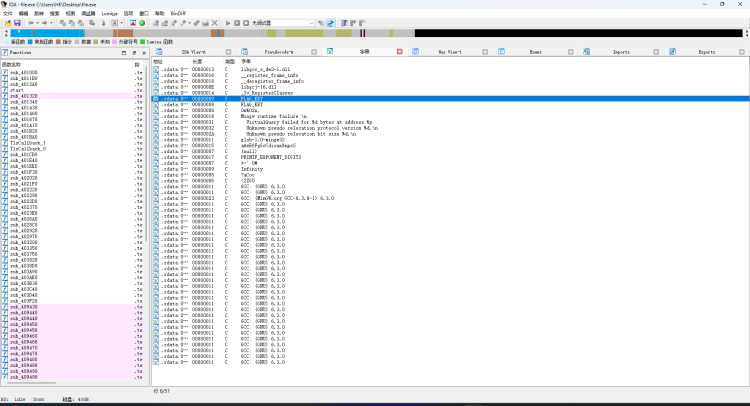
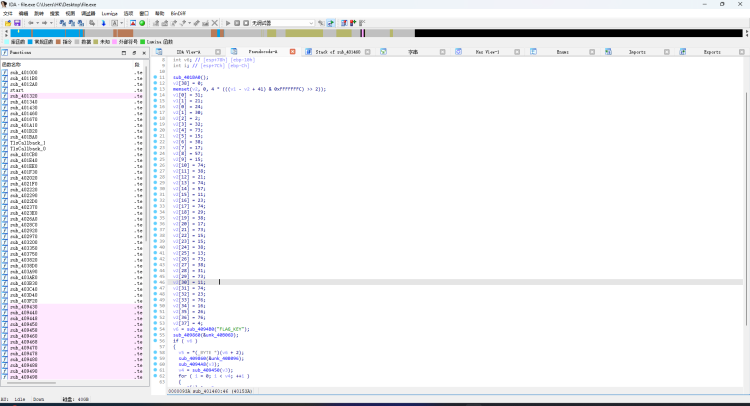
根据数据 逆向出key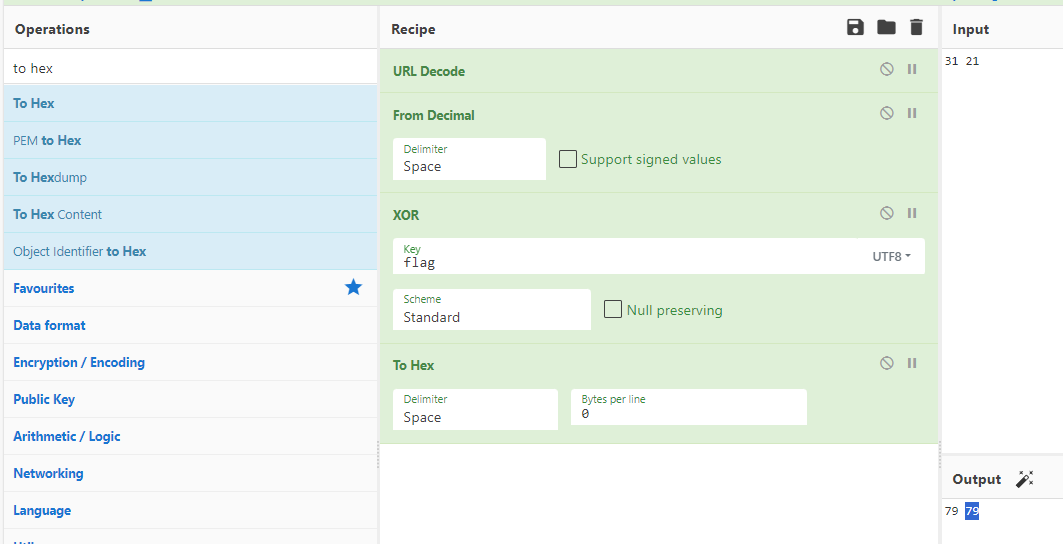
1 | data = [31, 21, 24, 30, 2, 32, 73, 15, 38, 17, 57, 15, 74, 38, 21, 74, 57, 11, 23, 74, 29, 38, 17, 73, 15, 15, 38, 13, 73, 38, 31, 73, 11, 74, 23, 76, 16, 26, 76, 4, ] |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 IHK-1's blog!